Installation and management of SSL certificates are a source of confusion and frustration for many sysadmins. This is especially true for those who manage only a few websites. Here we cover how to add an SSL certificate to a website and check the configuration using a free certificate from Let’s Encrypt. The configured SSL certificate will grade A+ on the Qualys SSL Checker – with the caveat that standards change faster than our posts. We’ll plan to revisit the configuration and update the article when there is a change in scoring.
Target Environment
For the hosting environment, let’s focus on the latest LTS version of Ubuntu running Nginx. You aren’t running Apache anymore, right?
- Ubuntu Server 24.04 LTS
- Nginx Web Server
Installation and configuration will require root access to the server via console. The server needs to be be publicly accessible on the Internet on port 80 (HTTP). A text editor is used to update configuration files. Nano or vim will do the trick.
Site Configuration
The first step is to get a clean sites-enabled (/etc/nginx/sites-enabled) configuration file for the target website. Clean out the configuration file, leaving the site running on port 80 on a fully qualified domain name. Confirm that the site is publicly accessible over HTTP at the desired URL. Use nginx -t to confirm that the configuration is valid.
Let’s Encrypt
Certbot is used for provisioning and managing SSL certificates from Let’s Encrypt, generously supported by the Electronic Freedom Foundation. The certbot package handles the certificates. The python3-certbot-nginx provides Nginx integration which handles most of the configuration requirements. Install the packages. I recommend adding the build-essential package if you don’t already have the prerequisites.
# apt install certbot python3-certbot-nginxCreating a Certificate
Assuming you have a website configured on Nginx, it’s time to create the certificate. Keep in mind that your website needs to have one or more fully qualified domain names in the server directive in your site configuration.
# certbot --nginxOn the first run, you’ll get some questions that required a response. Answer as you see fit, but going with Yes is generally a good idea. Certbot will also ask for an email address that is notified of issues and expirations. This is a server-wide configuration, so choose an email address that applies to the server instead of the specific website.
Certbot will then present a list of available website URLs. Enter the numbers of the websites that share a sites-enabled configuration file that should share a certificate. Certbot will then provision a certificate, update the site configuration file, and schedule the certificate for automatic renewal. Assuming that the certificate creation was successful, the website should now be accessible over SSL. Check it in your browser.
Locking Things Down
The recent versions of Certbot do a great job of configuring a secure SSL certificate. It’s worth taking a look at the updates that it makes to understand the criteria for a secure SSL installation.
Inspecting the site configuration file will show that Certbot inserted a few configuration changes when adding the certificate. The site is configured to redirect all HTTP traffic to HTTPS. The main server block has been changed from listen 80; to listen 443 ssl; followed by links to the certificate files. Finally, Certbot adds configuration hardening directives in the form of include /etc/letsencrypt/options-ssl-nginx.conf; and ssl_dhparam /etc/letsencrypt/ssl-dhlparams.pem;
All of these lines are suffixed with # managed by Certbot to warn users to not muck around with them.
The two files do the heavy lifting of SSL hardening automatically. The ssl-dhlparams.pem file contains a larger than default Diffie-Hellman key to make security scanners happy. The options-ssl-nginx.conf file turns off legacy encryption algorithms and weak ciphers. Here’s what options-ssl-nginx.conf contains.
ssl_session_cache shared:le_nginx_SSL:10m;
ssl_session_timeout 1440m;
ssl_session_tickets off;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers off;
ssl_ciphers "ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384";You may notice that the directions in options-ssl-nginx.conf also appear in the standard nginx.conf file with different values. The include file overrides the settings based on its placement in the server directive.
Grading an SSL Certificate
Qualys provides an online SSL Server Test evaluating the validity, chaining, and security of the certificate. Entering the website URL will start a scan and produce a report with security grade. An out of the box Certbot certificate should score as an A. Any issues and limitations are described in the report.
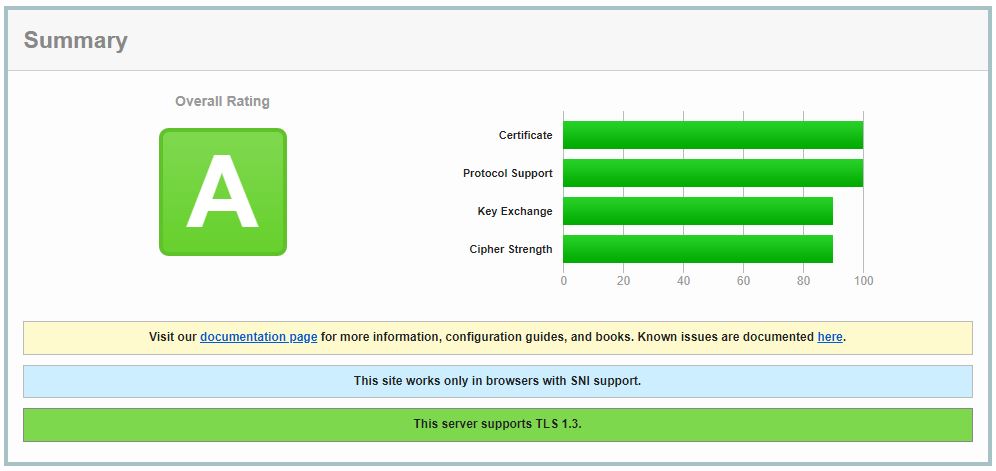
Going from an A to A+
Getting an A+ requires a modification to the site configuration. Add the following line to the site configuration file. Above the listen 443 ssl; line is a good spot.
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload";Server headers provide hints to the browser on how to communicate with the web server. The Strict-Transport-Security header helps prevent man-in-the-middle attacks by blocking protocol downgrades. The header declares that clients are only allowed to connect to the server using HTTPS as outlined in RFC-6797.
Reload the site configuration with service nginx reload and head back to Qualys to re-score the website. Run a new test or clear the cache on the previous test to get an updated score.
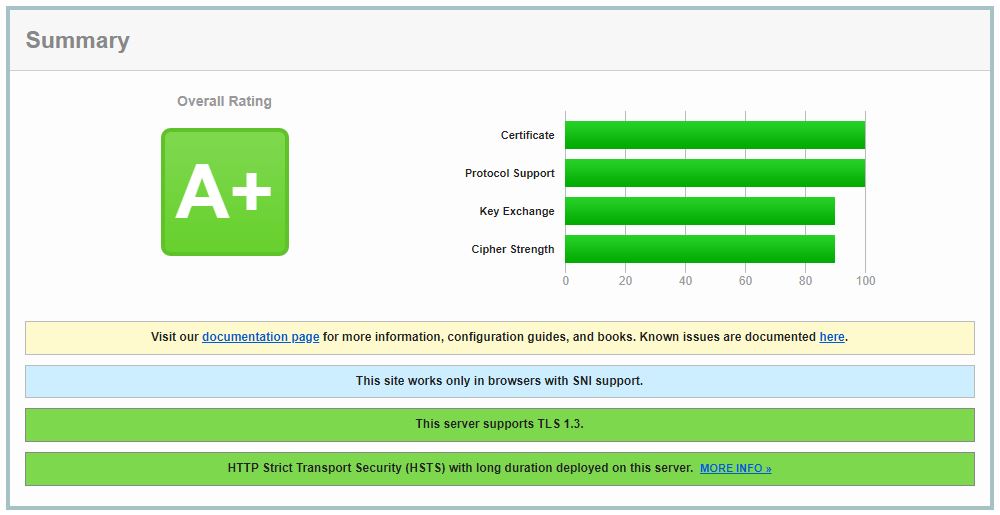
In Summary
The EFF has achieved its goal of helping secure the web by providing simple tools for creating and managing SSL certificates. These tools remove the costs and excuses for most configurations and pushes the bulk of web traffic over encrypted channels. Every website administrator should do their part by properly deploying Let’s Encrypt certificates and chalk up an A+.
What About My Web Configuration?
Scoring an A+ on Qualys for your SSL certificates comes down to disabling legacy encryption algorithms and forcing communication over SSL. With a bit of additional investigation, most web administrators can adapt these instructions to their web configuration. However, SSL remains troublesome and frustrating for many site admins. For different configurations or problem installations, contact SANCSOFT at inquiries@sancsoft.com. We provide assistance for proper SSL configuration on servers, cloud deployments, and embedded systems.
